Uncompromising Passwords (and More)
Working Together to Keep Your Website Secure
Most web hosts these days, particularly those who are hosting WordPress sites, are forward-thinking when it comes to site security. Yet we sometimes still hear the occasional horror story about a compromised website and wonder, “how did this happen?”
Unfortunately, the common cause of many compromised sites isn’t a particular web host, technology, or site purpose — it’s the person who is updating their website.
If you are hosted by a company who is supporting and maintaining your website (such as RainStorm), they are regularly updating your core WordPress software and plugins to their latest versions. Typically, they are making regular backups of your site, as well as maintaining an archive, so if there is any issue, they can restore a previous version. And they are likely hosting in an environment that has the kind of security that makes WordPress most successful.
What Happened to Me?
If you have taken all of these steps, how did the hackers gain access to your site? Usually, the answer is regrettably simple: weak passwords and bad WordPress plugins.
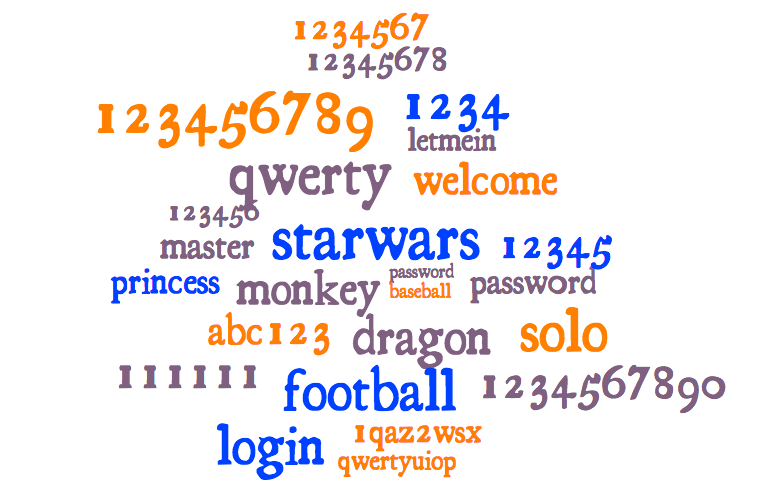
Here are some of the most common passwords ever. If your password is on this list don’t even finish this post – go change it now and come back. We’ll still be here!
But How Do They Know My Password?
We are all too familiar with stories of hackers gaining access to the user information of big corporations via a data breach. When that information is sorted, patterns emerge, showing what kind of passwords are most common (and boy, some of them are very common!). Often your site isn’t even the target of the attack — your website is just a means to an end, and you happen to be the easiest access point.
Lists generated from these patterns are used to teach web robots AKA “bots” (simple computer programs used to perform highly repetitive operations) to trawl the internet and enter data into online forms, including website logins. Large numbers of bots converging on a single site and using this trial-and-error method is called a brute force attack. Sometimes it becomes clear from the data that an individual uses the same password, or variations of it, on multiple sites, and this can be exploited by unscrupulous individuals.
Using a weak password for your website is like protecting your house with one of those locks you can easily open with a hair pin. Sometimes it’s like just leaving the door wide open! It’s not secure enough and leaves your site vulnerable.
And What About Plugins?
Plugins are small pieces of software that add functionality to WordPress websites. From email sign-up forms to shopping carts; plugins exist to help make WordPress sites more powerful.
But we all know the saying: with great power comes great responsibility. If you have a web host maintaining your site, they should be updating the plugins regularly, because outdated plugins are another way that sites can be exploited.
We suggest working with your web developer to vet plugins used in your site. At the very least, be sure that you’re using plugins that are made by reputable developers. It may mean choosing a paid plugin over a free one, but really, isn’t your site security worth it?
 Guidelines for Reducing Risk
Guidelines for Reducing Risk
- Choose a username that’s distinct (no admin or administrator)
- Use a complex password – one that’s complicated, long, and unusual
- Pick a random string from 8-20 characters long, including lower and uppercase letters, numbers, and characters (brute force hardware and software can unscramble anything less in seconds)
- No repeated letters, numbers, or characters
- No sequential numbers or letters
- Nothing that’s personal (dates, names, places)
- Do not use any of these passwords
- Keep passwords secure and private. Don’t store passwords where someone could get to them (a low-tech piece of paper is one of the most secure ways to keep track of them!)
- Use one password per website or application – no repeats.
- If you must store passwords online, use a password management service
- Restrict “admin” privileges for only those who need it, and use other WordPress user roles that are appropriate for each content manager’s needs
- Work with your web developer to review plugins annually
- Choose only well-supported plugins which match the most recent version of WordPress and have been updated within the past year
If your site is compromised, get the assistance of your web host immediately. They’ll want to know, to the best of your memory, when the site was last seen in its proper form so they can restore it, and check for any malicious code that might have affected your information, and possibly identify what weakness enabled the compromise so it can be taken care of.
Ideally, using some of these techniques, you’ll be able to keep unsavory characters out of your website and keep it up, running, safe, and healthy for your visitors for the life of your site!
